This post, we take a look at Botnets: what they are, how they work, and how they are shaping the foundations for future software security efforts. A botnet is a collaboration of many computers working together to accomplish a task. On the face, this seems harmless enough. When one considers that most botnets are built to function without the knowledge or consent of the computer owners, it becomes clear that botnets are the technical backbone of online criminal efforts.
The first significant botnet to adversely effect the Internet dates back to 1988, when a Cornell university graduate student launched a worm in early November from a campus of MIT. The program he wrote was more an experiment gone wrong than it was an illegal venture. In summary, Robert Morris built a self replicating worm to try to determine the size of a network of computers that most Americans didn’t even know about: the Internet. The experience set a number of precedents: the first botnet was built, the first conviction came under the US Computer Fraud and Abuse Act of 1986, and the establishment of the US Computer Emergency Readiness Team (CERT). In the end, the grad student was sentenced to 400 hours of community service and paid a USD $10,000 fine.
SOURCE: Washington Post, Business Insider, Daily Beast
Botnets have inspired terms to help describe who controls them and how they are used.
- Bot: A web robot program that performs a processing task and communicates the result over an Internet connection.
- Trojan: A program that appears to be either a utility or a beneficial update. The contents, instead hold a malicious package that infects a computer and adds it to a network of illegally purposed computers.
- Zombie: An infected computer under the control (not owned) of a cybercriminal.
- Botherder: A person who looks after (updates) the malware in the botnet and is either a cybercriminal by choice or by association.
The folks at the National Cable and Telecommunications Association have a good infographic on how botnets work:
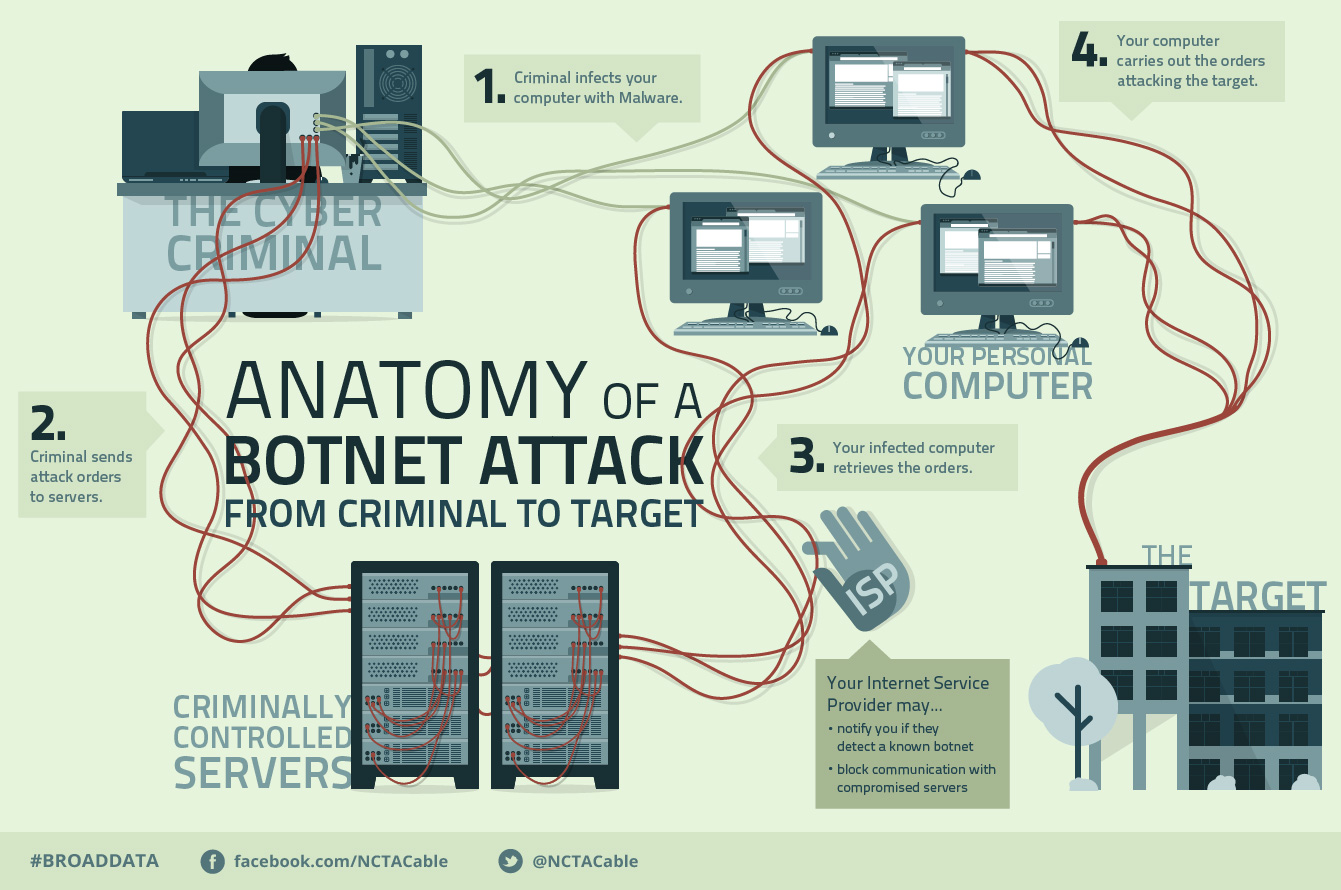
One of the easiest and most reliable ways that a botherder controls his network of zombies is through Internet Relay Chat (IRC). More and more, the servers that use IRC are classified as Command and Control (C2) Servers. A large number of these C2 servers operate out of eastern European countries with Russia being at the top of the list. IRC was initially unencrypted, but as malware evolves, the IRC commands are increasingly being sent as encrypted messages over https (secure) connections. Additionally, the communications are routed through the Deep Web over anonymous networks, like TOR, to help mask or deflect surveillance efforts.
Why would anyone want to put the effort into building a large network of computers to help them carry out illegal activities? Botnets are a budget supercomputer. By using the combined processing capabilities of several hundred computers, cybercriminals are able to “capture” processing power without paying for the operating cost, maintenance and upkeep, or risk of being shut down. By taking advantage of the human tendency to see online security risks as “someone else’s problem”, botmasters and botherders are able to consistently perpetuate low-cost or no-cost botnets.
Botnets make security an urgent threat to all. Companies and large enterprises need a robust protection capability. This is often found in real-time analytical software that provides intrusion detection and a “sandbox”. By creating a space to limit what inbound programs or new software can do, patterns of attempted behavior can be observed. In many recent cases, time is an element of the design of the botnets. They perform many functions repeatedly in order to undo the effects of anti-virus and intrusion detection protective systems. The sandbox helps to contain the software and provide response time to the targeted company.
- Individuals can take a few easy steps to help keep botnets from snagging a computer at home.
- Install anti-virus software and keep it up to date with virus definitions from the software vendor.
- Be very cautious with external devices like flash/thumb drives. Use encrypted flash drives that require a password to save anything onto them.
- Do not turn off firewall or other protective network systems. Even short periods with no firewall protection can allow a botnet to find a way in.
- Use strong passwords and do not share them.
ABOUT THE AUTHOR
Christoper Watson is an Information Technology professional with success in both public and private sector businesses. Technical and business experience is complimented with operational and strategic planning, international contracting work, leadership development and team building competency in challenging physical and political environments. Experience leverages strengths with technology services and providing timely and relevant information to senior executive leadership. Christopher is based out of the Oklahoma City office.






Leave A Comment