Our Blog
The Basics of Internal AI for Businesses
The Basics of Internal AI for Businesses Artificial Intelligence is all [...]
5 Steps To Get “Remote Ready”
5 Steps To Get "Remote Ready" Top of mind for organizations [...]
How To Get Hacked
How To Get Hacked: A Quintessential Guide Life’s a breach! [...]
Public Folders, Now You See Them…
Public Folders, Now You See Them... A Tale About Missing Public [...]
5G, Low Earth Orbit and URLLC
5G and Low Earth Orbit We recently posted a blog article [...]
5G Wireless Networks
Welcome to 5G By the end of this year (2018), the [...]
Hijacking Border Gateway Protocol
Hijacking Border Gateway Protocol Welcome aboard Our information travels as much [...]
Remove RDP Warnings Using SSL Certificate for Windows and Fortinet
SSL Certificate For Windows & Fortinet How to Remove Those Pesky Warnings! [...]
It’s About Time: Passwords and What it Takes to Break Them
It's About Time: Passwords and What it Takes to Break Them [...]
The Digital Zombie Apocalypse: Is Your Computer a Zombie?
The Digital Zombie Apocolypse: Is Your Computer a Zombie? As we [...]
Delete Files with Long Path Names
Ghost in the Machine – Delete Files with Long Path Names [...]
Tips to Secure Your Smart Home
Tips to Secure Your Smart Home Spending my days working in [...]
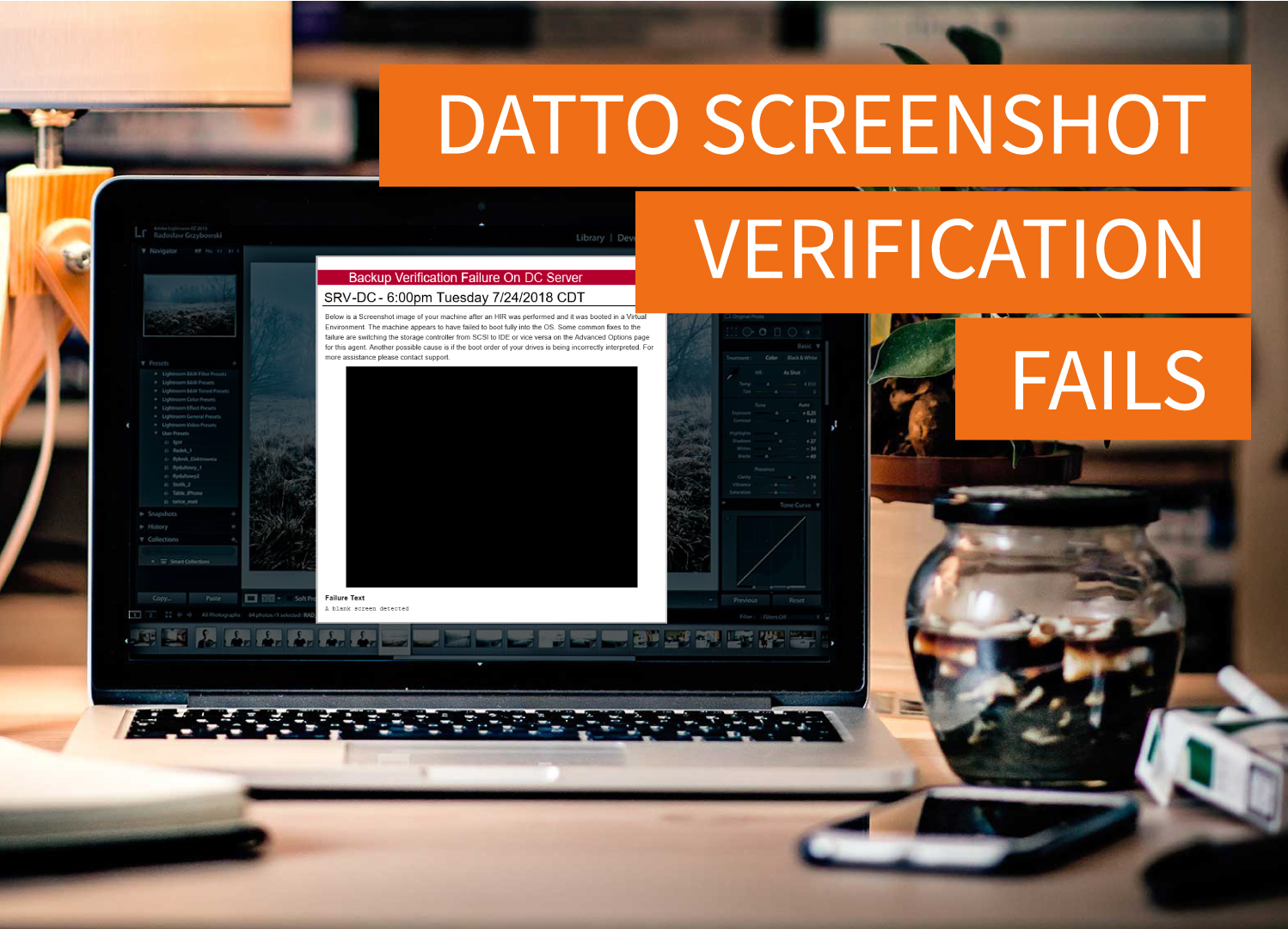
Datto Screenshot Verification Fails
When Datto Screenshot Verification Fails - Flux Capacitor Error In the movie, Back [...]
Managed Services IT vs In-House IT
Managed Services IT -vs- An In-House IT Pro For small to mid-sized [...]
How to Decommission a SBS Server
We recently migrated a client from an SBS 2008 environment to a Server [...]
How to Prepare for Windows 7 End of Life
If your doctor told you that unless you made some changes [...]
How To Resolve Broken Domain Trust Using Powershell
So recently I endeavored to repair a Windows 10 PC. There were some [...]
In Search of the Alt-Click Menu in Office 2016
So, you’ve decided to roll-out Office 2016 to your users, and you want [...]
Server 2003 NTBackup Alerts
So it’s 4:00 on Wednesday afternoon, and you have a print server with [...]
Stuck on Public Network Locations
One issue that has frustrated me a number of times is having a [...]
Backup Alerts: Optical Illusions in Consciousness
Have you ever been in a server room that had you scratching your [...]
The Ramparts We Watch
How to Allow Legit Network Access Through Your Firewall Is your firewall [...]
Is Your Business Ready for Disaster Recovery?
As a solution provider who helps IT organizations keep up with the ever-evolving [...]