You’ve set up your infrastructure to provide the most productive work environment possible for your users. You adhered to company management and IT policies and created a system to control access to the Internet for the company’s and user’s protection. Then you discover someone found a way to bypass those controls. Welcome to today’s world in IT administration. Managing your users is not too different from parenting your children. They are going to test the boundaries. If they can, they will.
I recently had been tasked with preventing users from installing and running Google Chrome. This company had an extensive Group Policy system in place to control how users are able to access the web via Internet Explorer. Whether or not it was because an astute user discovered they could bypass those controls using Google Chrome, or it was just “automagically installed”, it was against the company’s IT security policy. These users do not have local administrator permissions on their machines, but alas, that is not necessary to install Chrome. Standard users can install it. Google Chrome installs to the user profile, in the \AppData\Local folder rather than the Program Files folder. Users have full administrative rights to their profiles folder, so therein lies the problem for us hall monitors. This is where Group Policy Software Restriction Policies come to the rescue to block Google Chrome from installing and running.
How to configure the policy to block installation of Google Chrome.
- Edit or create a new GPO contain the settings to disable Chrome.
- Navigate to User Configuration -> Windows Settings -> Security Settings
- Right-click Software Restriction Policies, and select New Software Restriction Policies.
- Right-click Additional Rules, and choose New Path Rule
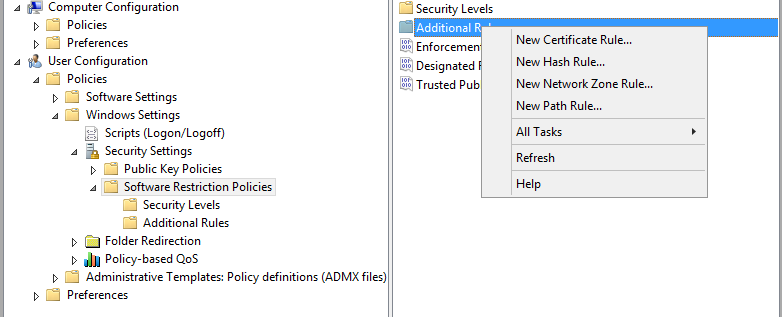
- In the Path field, type exe.
- Select Disallowed in the Security level drop down menu, and click OK to save the rule.
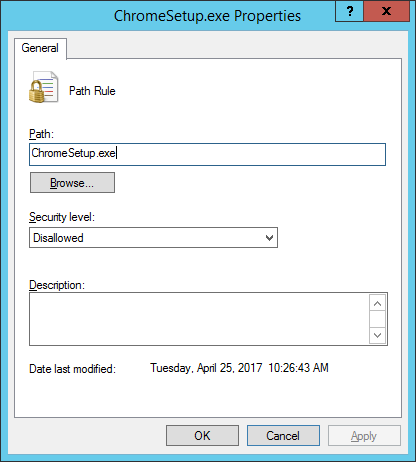
- Add the following rules by repeating steps 4-6:
- Chrome.exe
- Gears-Chrome-Opt.msi
- Chrome_Installer.exe
- GoogleUpdate
- C:\Program Files\Google\Chrome\Application
- C:\Program Files (x86)\Google\Chrome\Application
- C:\Users\%username%\AppData\Local\Google\Chrome\Application\Chrome.exe
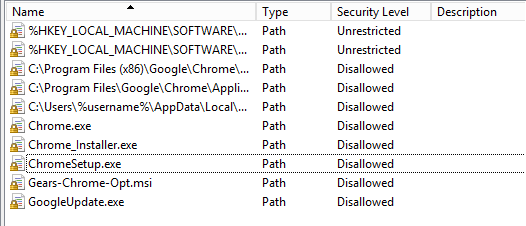
- When complete, this is how the Additional Rules in your Software Restriction Policy should look:
- Link the GPO to the domain, or for more refined restriction, to a specific OU.
- If you should need to also block Mozilla Firefox, you’ll need to create 2 rules with these Paths:
- Firefox exe
- Firefox Setup*.exe
Installation of Google Chrome will now be disabled, and users will receive a notification that their system administrator has blocked the program. But now what do you do for admins or web designers who have permission to run Chrome, or other web browsers – for testing or whatever the need may be? Fortunately, you can control how Group Policies are applied by filtering the scope of the Group Policy Object. I need to point out that this process should be performed using group membership rather than individuals to simplify administrative overhead of keeping the filtering up to date. The following steps contain additional configuration for allowing Chrome access for specific groups.
How to allow Chrome access for specific groups.
- To exempt a group from being blocked, for example, Domain Admins, delegate permissions.
- In the GPO, on the Delegation tab, click on the Advanced
- Select the target group in the top window, and scroll down to Apply group policy in the bottom window, and check the box under Deny. Click OK.
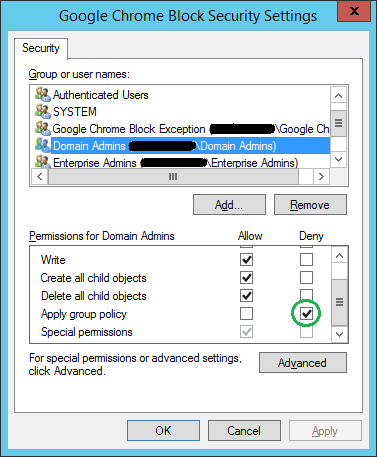
- In the example above, I also created an AD security group, Google Chrome Block Exception, and added it by clicking the Add button. Then, I denied the policy from applying by checking the box. This group allows us to add members who need to use Chrome, but we don’t have to make them a Domain Admin.

You have now disabled Google Chrome for all users that are not specifically allowed access to it. At the end of the day, it’s just another tool we system admins have in our arsenal to combat the introduction of unauthorized applications into our network. That could compromise the security and productivity we’ve implemented in our network, which might make the end of the day come much later.
About the Author
Donny Hilbern is a network and systems consultant specializing in analyzing, designing, and implementing network and enterprise systems. Donny has been working in the IT field for over 25 years, with nearly 20 years of that time invested in network and system administration and infrastructure technology. He has experienced a number of undocumented or lightly documented issues during that time. His desire is to leverage that experience in sharing about some of those issues and how they were resolved to make IT work for his clients.






Unfortunately, installation is still permitted. The user just can’t launch it. After time, this still leaves vulnerabilities detectable on the system due to an old version without some additional cleanup. Ideally, installation would be prevented entirely.
This may be due to the fact that Google changes filenames of their installers from time to time, and we also need to add another installer to the list of rules. Google’s standalone installer has a different filename, ChromeStandaloneSetup*.exe. The wildcard should satisfy the 32 bit and 64 bit installers. This should also close another security hole, in that a savvy user could obtain the offline installer on removable media and subsequently use it to install the standalone version of Chrome. There will probably be others we’ll have to add from time to time. Keep in mind Microsoft and Google are playing a virtual chess match. You find a way to bypass security, I’ll patch the hole. Oh, yeah, patch that hole, I’ll expose another one. One upmanship at its finest. Somehow, I don’t think we’ll hear “Checkmate” any time soon.
Hello,
I tried to set this up, unfortunately with little success.
The GPO and its settings did apply to the test device, as I first thought the issue may be caused by the GPO not applying.
Can I ask what setting did you use for the default security level ?
There are three levels to be chosen from as one will be the default sec level under
user configuration -> policies -> windows settings -> security settings -> software restriction policies -> security levels
you have disallowed, restricted and basic user
Or even more handy, is it possible to provide a overview of the settings of this policy ?
thank you in advance
i meant unrestricted* for the second sec level , sorry
I understand this post was written in 2018. It may seem like old news, however your page still comes up in my bing searches. Therefore, it is probably still being read. With that as a backdrop, I want to suggest there may be another way to accomplish this. Google can name their installation whatever they want but they are always going to sign their installer with a certificate issued by Google LLC. If you refuse/block the certificates they use to sign their code or, better yet, refuse the signing certificate they use to issue all their certs, I believe it would be even more straightforward to refuse running executables published by Google. I have not tested this, but I believe an approach like this could be an easier way to block programs from a legitimate company. Obviously, blocking programs from a company that doesn’t sign their executables is much less straightforward.
Appreciating what Allan has suggested, there is a way to manage this in group policy; AppLocker
You can deny and allow on a slew of options in addition to the published i.e. paths, filename, application name, version etc.
Make sure you populate all rule sets with the default rules while you test, it will/can break your start menu if you don’t.
AppLocker may well be a better way to accomplish this today, although I have not tested it with Chrome. I have used it with other applications, and Chris makes a good point. Be careful with your rules in your testing or you’ll be beating your head against the wall trying to figure out why it breaks.